
With WordPress websites, along with brute force login attacks, one of the most common types of attack that can cause downtime for your site is with the XMLRPC.php file.
The XMLRPC file is used to allow remote connections to WordPress, and is most commonly used when you use the Android or iOS apps for managing your website. It is also commonly used for functions in the JetPack plugin. If you do not use either of these on your website, then disabling it will do no harm. This can be done by adding a simple “die();” command at the top of the php code within the xmprpc.php file, however this would be overwritten when WordPress updates.
To avoid having to add that code every time you perform a WordPress upgrade, I have the following solution for you if you are using a cPanel based hosting environment.
1. Create a 404.txt file
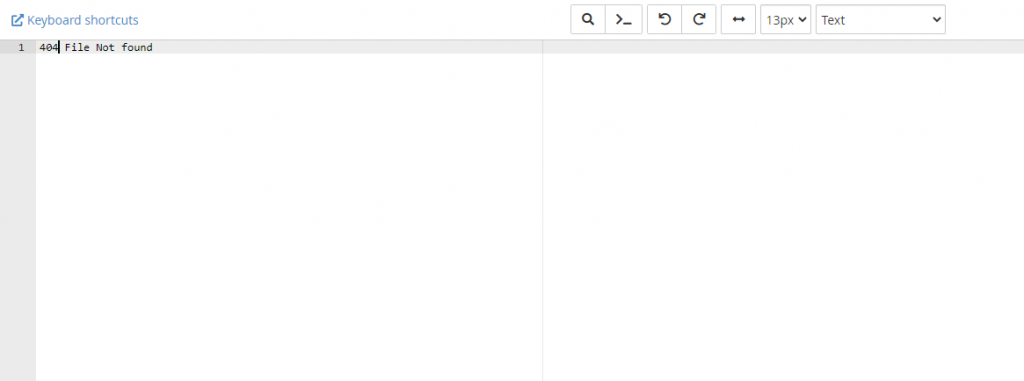
Within your sites public_html directory, create a file called 404.txt – The file can be empty, or can contain some plain text such as “404 File Not Found”.
2. Add a redirect to that file at the top of your sites .htaccess file
RewriteEngine On
RewriteCond %{THE_REQUEST} xmlrpc.php [NC]
RewriteRule (.*) https://exampledomain.com/404.txt [R=301,L]
This code will redirect any request to the xmlrpc.php file to your text file and stop any PHP processing from occurring on requests to that file. It works regardless of whether your site is installed in a subdirectory or in the sites document root.
Hope this helps you as much as it helped me.


Leave a Reply